Only When Logging on With an Account That Is a Member of the Administrator's Group Can You Do This.
Managing local groups on domain members via GPO restricted groups
From SambaWiki
Introduction
AD administrators often have the requirement to manage local grouping memberships of Windows workstations and servers from on a cardinal fashion. Group Policies Restricted Groups is a simple way to reach this requirement and works in a Samba Advertizing equally well as in a MS controlled.
Restricted Groups are non-tatooing changes. This ways, if you undo this change in the GPO, the changes are reset to their previous land on the affected computers after the next GPO refresh.
A all-time do is, to employ only AD groups instead of individual user accounts, to add to local groups. This allows changes on a central place (Advertising), by adding/removing members to/from the group, instead of modifying the GPO.
For simplicity, all examples in this documentation are configured on domain level through the Default Domain Policy. Needless to say, that is possible in self-created GPOs and OU-level, too.
Preconditions
- Installed Group Policy Management Panel. It is part of the Remote Server Administration Tools (RSAT).
- The examples used below add a AD domain group „SAMDOM\Wks Admins". Groups tin be added to the AD using 'samba-tool' or Active Directory User and Figurer (ADUC).
Change local group membership and proceed existing members
This is the most typical field of application: An Advert group should be added as a member to a local grouping and all already existing members should exist untouched.
Instance: The AD domain grouping „SAMDOM\Wks Admins" should exist added to the local „Administrators" group on all computers in the domain (workstations and server). The members of this domain group can be managed centrally in Ad and allows member accounts to accept local administrator permissions on all Windows computers, without knowing the Domain Administrator password or being member of the „Domain Admins" group. All existing members in the local „Administrators" grouping should stay. Simply the domain grouping „SAMDOM\Wks Admins"should be added.
- Create a domain group „Wks Admins", using 'samba-tool' or Active Directory Users and Computers from the Remote Server Administration Tools (RSAT).
- Open the Group Policy Management Console
- Select the "Default Domain Policy". Verify that the "Authenticated Users" principal is listed in the "Security Filters" list (this is the default). If the principal is not part of the list, add it. In case you lot removed this principal intentionally, you must alternatively add together the computer account(s) to the list and grant "read" permissions. For details, encounter MS16-072.
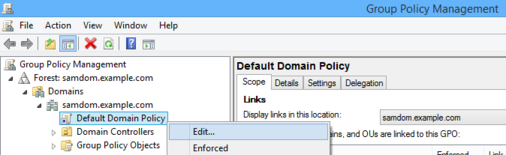
- Right-click to „Default Domain Policy" and cull „Edit..."
- The Group Policy Management Editor opens
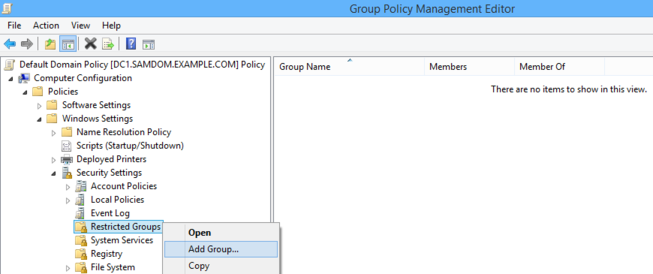
- Navigate and right-click to „Calculator Configuration" / „Policies" / „Windows Settings" / „Security Settings" / „Restricted Groups" and choose „Add group...".
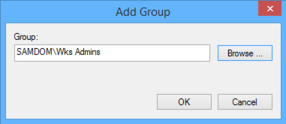
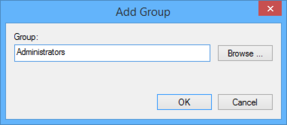
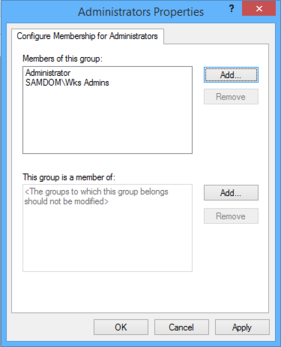
- Enter the name of the Advertizement group „SAMDOM\Wks Admins" by browsing your directory and click „OK".
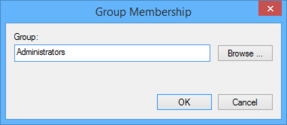
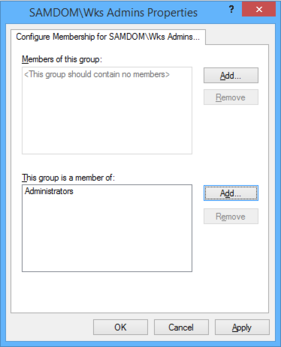
- The properties window opens. Click the „Add together" button next to the „This group is a member of" box.
- Enter the local „Administrators" group proper name. If you use the „Scan" button, select the local computer, by using the „Locations..." push button in the upcomming window, to scan local instead of Advertizement security objects!
- You see the local „Administrators" group entry in the „This group is a member of" list.
- Click „OK".
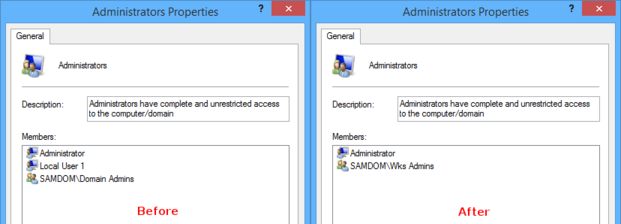
After the clients have re-read the inverse group policy, the domain grouping „SAMDOM\Wks Admins" volition announced in the local „Administrators" group on each customer afflicted by the GPO. All existing members of this group stay untouched.
Explicit control of local group membership
This way describes how to explicitly set the membership of a local group by replacing existing memberships with the ones divers in the GPO. Employ this with care, to ensure that you don't intermission existing permissions of accounts used past users and applications!
Instance: On all figurer in the domain (workstations and servers), the local Administrator and the domain group „SAMDOM\Wks Admins" should be the simply members of the local „Administrators" group. All existing members of this group should be removed and only these two objects should exist office of information technology.
- Create a domain group „Wks Admins", using 'samba-tool' or Active Directory Users and Computers from the Remote Server Administration Tools (RSAT).
- Open the Group Policy Management Console
- Select the "Default Domain Policy". Verify that the "Authenticated Users" main is listed in the "Security Filters" listing (this is the default). If the principal is not part of the list, add together it. In case you removed this principal intentionally, you must alternatively add the computer business relationship(southward) to the list and grant "read" permissions. For details, see MS16-072.
- Right-click to „Default Domain Policy" and choose „Edit..."
- The Group Policy Management Editor opens
- Navigate and right-click to „Figurer Configuration" / „Policies" / „Windows Settings" / „Security Settings" / „Restricted Groups" and choose „Add group...".
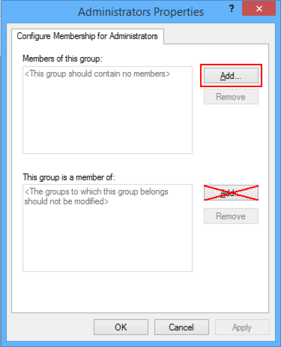
- Enter the local „Administrators" group name. If you use the „Browse" button, select the local computer, by using the „Locations..." button in the upcomming window, to browse local instead of AD security objects!
- Click the „Add together" button next to the „Members of this group" box.
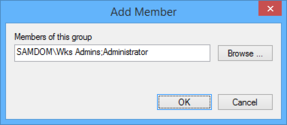
- Enter the domain group „SAMDOM\Wks Admins" and the local „Administrator" account. If you use the „Browse" button, select the domain/local figurer, by using the „Locations..." push button, to scan the domain/local security objects!
- You see the local „Administrator" account and the AD group „SAMDOM\Wks Admins" in the „Members of this group" listing.
- Click „OK".
After the clients take re-read the changed grouping policy, only the local „Administrator" account and and then domain group „SAMDOM\Wks Admins" volition appear in the local „Administrators" grouping on each customer affected by the GPO. All previous members have been replaced by this new members.
Strength manual group policy refresh
Windows computers refresh and utilize group policies on changes per default every 90 minutes with a random outset of 0 to xxx minutes. Run across http://technet.microsoft.com/en-us/library/cc940895.aspx.
To see if changes took event, you can force an immediate refresh of all GPOs on a host by running:
> gpupdate /force /target:calculator
The „/target:computer" option reads simply the „Computer Configuration" part of GPOs.
Source: https://wiki.samba.org/index.php/Managing_local_groups_on_domain_members_via_GPO_restricted_groups


0 Response to "Only When Logging on With an Account That Is a Member of the Administrator's Group Can You Do This."
Postar um comentário